Tuesday, May 18, 2010
Miscellaneous things on my mind today
there'd be a better way to represent the signals from the inputs to
the first layer. Ideally, that'd involve getting the symbols to
correspond to a value on a meaningful range, rather than a set of
discrete values. Let's say I wanted to make that integer range
[0,2
Monday, May 10, 2010
Miscellaneous things on my mind today
--
Pondering a message passing communication system tuned for bulk data (parcel) transfer. Use an addressing system like email's: To:username@example.com
Sender, relay and recipient nodes operate on a load-sharing basis similar to BitTorrent. Where with email, a sender has a single SMTP target, this system might have multiple such targets, each of which serve as feeders for the destination recipient(s). Relaying nodes may cease feeding once either all recipients' nodes have full copies of the parcel, or once a TTL metric has been met.
Sender-signing should be explicitly supported, both as a means of ham/spam separation and as a means of authentication/accounting where necessary.
Parcel bodies should be compressed and encrypted by default.
--
Just got the geek necessities
The simple geek necessities
Don't worry 'bout your food or your hygiene...
--
If you're standing on Four Corners, and you do something that's a crime under each state's law, which state's prosecution takes priority?
--
I don't think backprop is relevant to the HMM->ANN mapping, because ANN construction is done as a component of its training, and weight adjustments are done incrementally as each node gains experience, by the node itself. No final "result fitness" observation is done, because the from-map ANN inherently evolves the same way the HMM would.
Actually, looking at it further, what I have in mind could be considered a variation of a "cascading neural network", except the weights aren't fixed on node creation. Also, I don't see reference to any types of networks that allow for deconstruction of nodes.
--
I like this way of posting my thoughts; it keeps me from being the uber-spammer on the social networks I'm in. Plus, it's like a serialization of free association in a palatable form.
--
Hm. German. shadenfrau. Heh.
--
Need to start carrying my 3e/PF books around. Or PDFs thereof.
--
Barcamp presentation ideas: 1) Rosetta Code and programming chrestomathy. 2) Wikis and more effective cross-referencing.
--
I once had a conversation with a guy I think might have been high, where we thoroughly enjoyed a conversation that didn't keep a single context and topic for longer than three sentences.
--
:wq
Sunday, May 9, 2010
To learn, to Create, to Think
To create: Think about different things at the same time.
To think: You'll have to figure this one out on your own.
--
:wq
Friday, May 7, 2010
Miscellaneous things on my mind today.
I don't think this is necessarily an efficient way to do it, but I think it might be an exact mapping. Cool. :)
If you want a second-order Markov model, use two nodes in your input layer, and use S1,S2 pairs for your 2nd layer, with a single-symbol set for your third. Definitely not a space-efficient way to do it, but also an exact mapping. If, after training (you have to get your symbol set from somewhere, which means you're going to grow your ANN as you build your symbol set), you're comfortable with the idea, you can cull your absolute weakest relationships from your 2nd-order set. Only cull as space limitations force you to, or you'll lose weak-but-significant relationships.
A 3rd-order Markov model would have three input nodes, and use S1,S2,S3 tuples for the 2nd layer, and a single-symbol set for the third. Again, cull as required.
For particularly interesting results, you can use a three-dimensional matrix I1 going to a 1st-order ANN mapping, I1 and I2 going to the 2nd-order ANN mapping, I1, I2 and I3 going to the 3rd-order ANN mapping, and map to the same output node for all three orders. (Or higher orders, if you have unbelievable processing and storage capability...)
--
I'm happy.
--
If every piece of software got as much detail-oriented attention to it as Toyota's code is getting right now, but *before* disaster struck, there'd be millions of happier developers out there, software wouldn't suck as much and development and debugging tools would be absolutely incredible (far beyond anything I've even heard of, including things like valgrind, lint and VS2010's rather impressive debugging aid feature set) as a result of finding ways to reduce developer time spent in analysis and bugfixing. If software were nearly as difficult to consider "ready for release" as hardware is, I think you'd see something akin to Moore's Law occur in software utility. (As a mixed metric of performance and feature set.)
People got used to mediocre software. They hate it, but they got used to it. As a result, software pricing models more or less standardized around writing mediocre software, and people get sticker shock when they hit a requirement for non-mediocre software. Put another way: "Fast, well, cheap" -- except that popular priority heavily weighs toward fast and cheap.
--
Flashbacks to Ender's Game when I accidentally try to call CString::GetBugger(). See also, Start->Run->%APPDADA% instead of %APPDATA%. Dargo, resolve his %APPDADA% for him!
--
:wq
Thursday, May 6, 2010
Things on my mind today...
What happens if you could influence the Shadow ships' pilot with LSD or PCP? (If you haven't seen through Season 4, don't bother guessing. If you don't know what I'm talking about, then nothing's spoiled.)
What happens if a vampire or lycanthrope bites a bio-tech vehicle?
I need to make a habit of going to work earlier so I can get enough hours in before early afternoon. OTOH, I've got a ton of vacation hours saved up, and that would be a worthwhile way to spend them. :)
I broke someone's nerd-o-meter today. I feel good.
I seem to be discovering something akin to alchemy and herbal remedies, but using fast and processed foods for ingredients. That can't be a good sign.
SanDisk seems to have abandoned the SD+USB product area. [trope]BigNo[/trope].
--
:wq
Monday, May 3, 2010
Dave, my mind is going. I can feel it.
but my heart is all a'flutter.
Wrote a line of code
but I can't write out another.
Gotta get my brain in gear
but it's slippin like it's butter.
If I don't seee Firefly soon,
I'll be drinkin' like a Mudder.
Tuesday, April 27, 2010
There's one kind of argument I particularly hate to have
What's frustrating about it is that it tells me there isn't a logical basis behind the defense of their position, but an emotional one, and logic is simply the mechanism being used to defend it. That means that they're exceedingly unlikely to ever change positions, unless and until that emotional basis is identified and resolved. That's pretty difficult to do when the person holding the position can't acknowledge the basis behind their core position.
The particular argument inspiring this rant was my expressed frustrations that AdBlock Plus is overly aggressive, and blocks the queries that build Amazon referral links--I was going to use those links in-line in on-wiki citations and user-recommended resource links. With ABP running, one gets a big, fat, red "Unable to retrieve data" blob of text. I'll have to mod the MW extension to deal with the error case.
Saturday, April 24, 2010
Wednesday, April 21, 2010
2.5" -> 3.5" internal bay adapter
Tuesday, April 20, 2010
Yup. That StumbleUpon surge changed things a bit.
Usually, it's a combination of two things: 1) a steady trickle of referrals from dozens of forums like Stack Overflow, Reddit and language-specific phpBB installs. 2) A lot more people add "rosetta code" or "rosetta" to their search queries; I get the impression that this method of learning how to do stuff is getting more popular.
So, yeah, the ambient traffic appears to have permanently bumped up a notch. This has happened three times before, that I can think of.
Monday, April 19, 2010
[TSoC] Automated virtual plays - machinema for the social web
Tie each Twitter or blog account to a character in the play. Now, how do you automate it?
I see three pieces that need to be addressed to cover each member cast:
(character)
(service)
-(account)
--(contacts/friends)
I see four bits of information that need to be conveyed for each active line:
(trigger time)
(service)
(who is the message directed at)
(the message)
Now, think about this. How would you organize this data?
--
:wq
Monday, April 12, 2010
[TSoc] Abusing TinyURL, bit.ly, and your browser--making the work someone else's problem.
So here's basis behind one of the ideas: http://www.translationparty.com
TranslationParty works by taking your English phrase, using JavaScript to call into Google Language Tools to convert it to Japanese, repeats the process back to English, and back to Japanese--on and on until it finds "equilibrium", or is confident the phrase will never reach it. Of course, it only works with English-Japanese translation. You'll notice, though, that it uses an identifier to allow it to recall previous "parties". I can show you one I just created a moment ago, by having you click on this link: http://translationparty.com/#7180967
They're storing the seed phrases in a database, so that visitors can refer back to them. That's fine, I suppose, but that database is eventually going to get large and expensive, and most of the past seed phrases will have been forgotten about in the mean time.
I showed TranslationParty to a couple folks last night, and they noticed it only did English-Japanese translation. I'd just hit on the idea of doing something like TranslationParty, but using virtualhosts to allow language selection.
en.ja.example.com would behave largely like the existing TranslationParty site.
ja.en.example.com would start with Japanese as the seed language, rather than English.
en.de.example.com would bounce between English and German
de.fr.example.com would bounce between German and French.
So, $1.$2.example.com would start with $1 as the seed language, and #2 as the intermediate language.
Problem is, I wouldn't want to store that database. It's largely a waste of server resources, considering most of it would be forgotten ten minutes after it was created. The obvious solution is to store the seed phrase as an HTTP GET parameter. http://en.ja.example.com/?seed=What%20lies%20in%2the%2deepest%20regions%20ones%20our%2memory would have "What lies in the deepest regions of ones memory" as the seed phrase, and be equivalent to http://translationparty.com/#7181046 ...
Now, that's a long, nasty URL, not suitable for copying and pasting in polite company, but it means that I don't need a database for these things. Besides, that's what bit.ly and tinyURL are for, right?
--
:wq
Tuesday, April 6, 2010
Sunday, April 4, 2010
What we owe Apple and Mac users
However, they've got one heck of a marketing budget, and they manage to make their products mainstream, or, at least, 'hip.' That's something I can appreciate. Why? Because if it weren't for Apple making their hardware and software hip, there wouldn't be the demand for lookalikes and workalikes that leads to products I *do* want to use to become available.
(Yes, the Newton was a failure, but Palm followed up on the concept and made a device I enjoyed using for years.)
Consider the iPod. MP3 players had already been around for a while, but they weren't big sellers. Along somes the iPod, which takes the MP3 player market by storm, and drives the expensive little lossy-audio playback device into popularity. People discover the convenience of having a few thousand songs in their pocket, and show off to their friends. Their friends like the feature set, but balk at the price tag. Along come the products by other manufacturers and vendors, with similar functionality[1] and a lower price tag, and those friends buy. Apple made the MP3 player popular.
The iPod went through a few iterations. It added video, then it added video.
Now we consider the iPhone. Smartphones have been around for far longer than the iPhone, but I normally only heard about them being used by big corporate and institutional types. You didn't get them unless you had a financially-driven need for them, so they were only marketed to the organizations with pockets. Along comes Apple, with their iPhone and their marketing budget, and it *sells*, despite being an open-developer-unfriendly platform. Same as with the iPod, they show their friends this cool stuff, friends want something like it, and so you get things like Android and Windows Mobile[2] getting bought at cell phone retailers all over the place. Meanwhile, people got used to touch screens and video interfaces thanks to things like the iPod Touch, so adding a phone to the feature set doesn't seem too odd.
Now look at the iPad. Everyone teases it. I don't want one, because I don't like the development environment. Everyone teased iPod, too. Tablet PCs are nothing really new, either; they've been around for over a decade. The first one I remember seeing had an 80486 processor, and it was used for mobile logistical record keeping. It ran Windows 3.1, and had handwriting recognition. More recently, HP and other PC vendors have been selling laptop/tablet convertibles. My mother had one. It's kinda fun to use. Yes, they were never really popular. That's why people keep expecting the iPad to fail. They forget that MP3 players weren't popular before the iPod, and that smartphones weren't core culture until the iPhone. I don't know if it's a marketing budget, superb planning or superb timing, but Apple tends to take a known concept and get it to sell.
I expect the iPad will sell nicely. It's like a supersized cross between an iPhone and iPod Touch, with the phone features pulled. What with the requisite technologies for AR getting better and better, I suspect I know where Apple would like to go next.[3]
[1] Greater in some areas, lesser in others. I don't want to debate it.
[2] Yes, Windows Mobile has been around for a while. I didn't say it was *created* as a response to the iPhone.
[3] And a brief plug for an anime I've been enjoying lately. Dennō Coil
--
:wq
Friday, April 2, 2010
[question] Testing Virtualized XP installs with more than two CPUs.
So what if you have a quad-core or dual-quad-core system, you're running some virtualization package (KVM, VMWare Server, whatever), and you want your guest XP Pro instance to have more than two cores? On QEMU+KVM, there's no way to lump virtual CPUs as cores on a virtual physical processor, and there doesn't appear to be one on VMWare ESX Server, either. So how would you do it?
The particular scenario, in this case, is automated testing of software that's supposed to run on XP Pro with systems between four and eight cores. While it stands to reveal interesting bugs, running it on only two cores is non-optimal.
--
:wq
Quote from my boss from a couple minutes ago
I don't know if I said it
So you'll have to have to ignore the repeat
But I need to make sure I said it
...I forgot what I was going to say.
Friday, March 26, 2010
[TSoC] [UPS, USB, X10] X10 UPS and USB power supplies.
* X10 was once used to allow remote control of power outlets. It operated by adding a small set of pulsed high-frequency modulations on top of your home's internal AC. Take a peek at it with an oscilloscope some time; it's pretty cool.
* UPS devices report themselves well over USB, but that takes up one of a computer's external USB ports.
* In most systems I've seen and built, there are spare USB headers left on the board after building a system.
Proposal:
Taking these three in context, consider having a UPS self-report its status by doing a controlled modulation of its AC output. Have a computer's power supply be capable of receiving and interpreting these signals. Have that power supply plug into a spare USB header on the motherboard, to provide those communications onward to the system.
Benefits:
* Avoid using an external USB port
* Allow multiple computers powered off of the same UPS to be simultaneously aware of their power source's state.
Drawbacks:
* AC output of UPS can't be a perfect sine wave, much as that would be ideal. (Though most output a stepped approximation, anyway.)
* Requires that the PC's power supply be able to interpret the signals.
--
:wq
Thursday, March 25, 2010
For the last time, no, I Won't be a fan of "Google Fiber for Grand Rapids"
I Won't become a fan of Google Fiber for Grand Rapids, for a couple reasons. Let's start with the big one: I don't want my Internet traffic primarily channeled by a company whose primary revenue source stems from figuring out how to show me the ads I'm most likely to click on. That's a very, very direct incentive for them to do traffic analysis and directly watch the sites I visit so that they can figure out what I'm interested in, and thus what I might buy, and thus what ads to show me.
No, AdBlock doesn't fix things; avoiding being shown ads wouldn't stop the incentive for analysis any more than a boycott on Wendy's for serving meat helps PETA.
I'm sorry, but I'm just not interested. Even if they promise not to do privacy-invasive things, they ultimately can't help it; it makes too much business sense for them to set up a transparent HTTP proxy and build up their Analytics and Adsense statistical bases. *I* would, if I were them. If they don't, then they're stupid; they would be ignoring the opportunity to blend together geographical and demographic awareness into their ad business, and sell localized Adsense ads with better accuracy than the ones you already see. (From Jenison, I get offers to "meet singles in Kalamazoo" ... Kalamazoo is a long ways away from me, but happens to be where the other end of this DSL connection sits.)
So, no, I'm not a fan of Google Fiber.
The second reason I won't become a fan of Google Fiber is the same reason I don't plaster my car with bumper stickers; I don't care to broadcast my taste, appreciation, like or dislike of every single cause, organization or business that flies across my radar.
--
:wq
Saturday, March 20, 2010
[TSoC] A different kind of cell phone service
If a cell service provider can provide phone service that costs the same whether you're on their towers or not, what's to stop a towerless cell provider from providing service using a phone that doesn't care whether it's connected to the service provider via CDMA, GSM or an encrypted SIP connection tunneled across Wifi or WiMAX? Heck, any of the existing SIP/IAX2 trunking providers could potentially expand into that arena, and people wouldn't necessarily require a POTS phone number to call or be called. (Though, rather than calling a Skype ID, someone could simply call me at phone.michael.mol.name.)
Admittedly, toggling between cell and 802.11abgn radios will reduce battery life, and the phone would have to be a tad smarter to manage more of the service provider hand-offs itself, but that price is already being paid by smartphone owners.
Ordinarily, I'd be one of those arguing back "you can take my landline out of my cold, dead hands", but I've somehow managed to never have a landline to my name, nor one that people call when they want to reach me since before I even turned 18. With the drop in landline usage, and the pervasive increase in mobile phone usage, it strikes me as imminently doable.
--
:wq
Friday, March 19, 2010
Have I fallen so far?
Water once obeyed my guidance, flowing through pipe, hose and tube before sprinkling me amidst glorious sunshine. Have I fallen so far?
The sands themselves once moved aside under my machinations; the formation rivers, gorges, dams and lakes occurred at my influence. Have I fallen so far?
The frozen wastelands would strip themselves bare, the ice and snow forming men as tall as taller than I was. Have I fallen so far?
The trees would shed their leaves, simply for my joy and benefit. Have I fallen so far?
Yes, I have fallen, but the world has turned up-side down. It is now my role to serve those who will come after me. I have risen far.
--
:wq
Thursday, March 18, 2010
[Photography] 16:9
When composing for 4:3, the rule of thumb is to divide your image into a 3x3 grid, and keep a distinct element of the picture in each grid component. I suspect that, in a 16:9 aspect ratio, the composition rule might best change to 5x3. I already know how I'd want to use the six extra grid squares in various centered and offset scenarios.
Anyone know of anamorphic lenses for photography? I haven't upgraded from my FujiFilm Finepix yet, so I'm pretty flexible as far as compatibility...
[Linux, libvirt, kvm, snapshots] Piecing together an open-source equivalent of VMWare Workstation
* Snapshots, full clones, linked clones
* Resize guest display to match viewer viewport. (I had to resort to some XML editing in order to get a video device I could make larger than 1024x768, and that's still not as nice as having the guest framebuffer resize automagically)
* Drag-and-drop between guest and host.
* Application-in-host (Workstation calls this "Fusion", and it's awesome if you need it. I still need to send that fruit basket to the couple developers who wrote that feature.)
* Suspend guest VM.
* Has D3D9 acceleration (for Windows guests on Windows hosts, which wouldn't work for me anyway), which is better than the no-graphics-hardware-acceleration I face with libvirt+kvm. (There is an SDL client, but libvirt's dynamic privilege toying with PolicyKit doesn't manage to get it to work on my system.)
Things that libvirt+KVM does better than Workstation (at least as of the latest version I have access to)
* Will give as many as 16 virtual processors to a guest.
* The VM definition file is XML, and well-documented on their website; manual tweaks are pretty easy.
* Has the ability to not affix a MAC address to a guest. While this causes Windows guests to destroy old NICs and create new ones every time you reboot, it will make cloning much easier.
So let's see what we can do about the things that libvirt+kvm doesn't quite do on it own yet.
D3D9 Acceleration
Not going to happen; host doesn't have Windows. On the other hand, I can put in another video card and give a guest VM direct access to it. I haven't tried it, but it could work, so long as I don't allow the host's X server to use that card.
Susped guest VM
Not going to happen until there's a to specify a file to hold a RAM image, at least. (I could easily see them mmaping that file, too; it seems like a perfectly kosher way to leverage the x86 MMU on 64-bit systems.) No such option exists, currently.
Application-in-host
On Windows and Linux guests both, this requires some awareness of and integration with the guest window manager. There are probably VNC servers that can handle that individually, and there are already VNC servers for both guest operating systems that will serve up individual windows. If you put a VNC client on the host in Listen mode, you could find a way to have every launched application connect to that client. It'd require some real script-fu in the guest, though, and there's also the problem that VNC doesn't support drag-and-drop between clients. (And typically isn't aware of it at all...)
Drag-and-drop between guest and host
That'd require some extension to the VNC protocol, so I can't do that right now. (OTOH, it would be a very, very good general enhancement to the protocol!)
Resize guest display to match viewer viewport
VMWare uses the same core protocol between its viewing interface and its virtualized video card, and its viewing interface supports the viewport and guest triggering each other to resize. (Admittedly, I don't know for certain that the viewport-triggers-guest event is communicated using the same channel.) It seems likely that it could be done, but will require an extension to the VNC protocol.
Snapshots, full clones, linked clones
Some of this is something I might actually be able to do soonish (and I'll certainly be working on it!) Linux has LVM, which, at the very least, will let me take a snapshot of a base volume, and do copy-on-write for maintaining things. I don't know that it will let me take a snapshot of a snapshot, though, or give me simultaneous r/w access to multiple snapshots of the same base view. If it does, that would put it pretty close to VMWare Workstation's capability. If not, it puts me closer to VMWare Server's. VMWare Workstation allows you to take a snapshot after running on a snapshot, which gives you base->snapshot->snapshot, and you can choose to run any of those you like without affecting the others. It also allows you to create a linked clone of any of them, which amounts to creating a snapshot that you can run at the same time as you run a snapshot from that tree. VMWare Server, on the other hand, only has two states for a VM: current snapshot, and current state. In VMWare Server, you can always replace your current snapshot with your current state ("Take snapshot") or your current state with your current snapshot ("Revert to snapshot"), but that's it.
Notice I'm not talking about VMWare Server ESX*; that beast's snapshot model is a little closer to Workstation's.
Out of all of these things, the snapshots and clones are the part I need to work on the most. Right now, snapshots and clones are pretty much the same thing; copy the disk image, copy the XML file, and modify the XML file to point to the copied disk image's location. That gets pretty expensive, diskwise, pretty fast. LVM's copy-on-write should help with that a lot. So would a filesystem with built-in deduplication, but ext4 (what I'm running on right now) doesn't have that. (I can think of a bunch of other reasons a filesystem with built-in deduplication would be awesome, too. Maybe I'll brainstorm on some different performance tradeoff option ideas in the near future.)
--
:wq
Tuesday, March 16, 2010
[Techtalk Tuesday] Bittorrent and swarm stability
Bittorrent chops up the data into multiple pieces, and then the various clients in the swarm play mix and match until they have all the pieces they need for a full copy. Then (if they're well behaved) they stick around for a bit longer and give more copies of the pieces to other members of the swarm.
When a client joins the swarm, it gets a mapping of all the pieces in the swarm, and a listing of who has copies of which pieces. It then asks whoever it can for the pieces it still needs to complete its copy.
The problem I've observed is that if one piece has copies in more clients than another piece, then that first piece will tend to be copied to more clients still, simply by being more available, while that rarer piece becomes more relatively rare. This causes data distribution in swarms to grow "clumpy", with the availability gap between the most common and the least common piece growing wider and wider. If the only copies of a piece exist on swarm members which already have full copies, and those members drop out, then the swarm can't form more complete copies until someone with a full copy rejoins the swarm. Meanwhile, the rest of the swarm members copy from each other until they're all not-quite-complete, but don't get any farther than that.
What I'd like to suggest are three changes to the Bittorrent swarm behavior, both on the "server" and "client" side of the connection.
The change to the client is pretty simple; look at the map of available pieces and nodes, and try to grab the rarest ones first. Even if the client is misbehaved and doesn't plan on contributing to the health of the swarm, it still makes sense to grab the rarest pieces before they may disappear.
The first change to the server is a bit trickier, and would require support from the client. If the client asks for piece A, the server should give it piece A--after it gives it piece B, which is currently rare in the swarm, and it knows the client doesn't already have it.
Aside from requiring the client to recognize that the data it was handed wasn't initially the data it asked for, I can see one other problem with the latter approach. If the client is already asking for piece B from another node, then getting a copy of piece B from the node from which it asked for piece A is a waste of time and bandwidth. It could inform the server which pieces it's grabbing, but that would also be loss to efficiency. A compromise might be met where the swarm would only support slipping in pieces from the rarest N% set of pieces, and so the client would only be inclined to report any from that set that it was already grabbing.
Varying the client's pull pattern to either fall within, overlap with, fall near or be distant from that N% segment each have their advantages and disadvantages, but I'm not sure which would outweigh the others. On one hand, avoiding the N% bracket is a destabilizing influence on the swarm, but saves incident overhead. On the other hand, favoring the N% bracket means the client grabs the rarest packets quickly, but increases the incident overhead. Favoring just outside the N% bracket means avoiding the incident overhead, but destabilizes the swarm, and makes the assumption that there are a number of "slipping" seeders.
The second change to the seeder side would be to *proactively* push data to other clients, based on observed connectivity--to some extent, each client is aware of the bandwidth and uptime of other clients. If a client is observed to have a lot of bandwidth available to it, or is observed to be a stable member at a lower level of bandwidth, it makes sense for the swarm to push rarer pieces to places where they can be copied from more quickly. (For the stable, low-bandwidth clients, this had the added benefit of reducing their particular risk of missing out on rare pieces even more.)
Just some thoughts...
--
:wq
Monday, March 15, 2010
Memetic Mutation
You know the rules, and so do I
A full mutation's what I'm thinking of
You wouldn't get this from any other guy
I just gotta tell you what I'm thinking
Gotta make you lose the game.
Unqualified domains
Now let's throw another domain in the mix, accessible over VPN. This domain is also unqualified, and let's call it y, and say it has hosts alpha, beta and gamma, for alpha.y, beta.y and gamma.y.
Now, in Windows, I can tell the system to try resolving unqualified domains with a domain of x first, followed by y. That way, I can ping alpha, and it resolves to alpha.y, and I can ping whiterabbit, and it resolves to whiterabbit.x.
Under Linux, when I try to ping gamma, it doesn't resolve, but when I try to ping gamma.y, it does. Under a Windows VM routed through the same machine, pinging gamma resolves to the same thing as gamma.y. How do I get the Linux host to exhibit the same behavior? (No, I'm not going to route the host's DNS through the Windows guest.)
--
:wq
Sunday, March 14, 2010
[StepMania] I've still got it. [blogging] LJ and ping.fm
I dropped into stepmania a couple weeks ago and got the compile issue resolved; they gave me a revision to update to that worked great. Saturday, I tuned the pad.
Fired up StepMania, and all was good.
I gave a run through a few DDR 2nd mix and DDR 3rd mix songs, Franka Potente's "Believe", and a couple variants of Sonic the Hedgehog songs. (Most of those songs make pretty good hard techno. I'd venture a guess it's because of the hardware they were originally written to play from.)
I've discovered that the only thing that really stops me from getting a good score on a five-foot song is how many songs I played leading up to it; my read speed and agility are good, but I need to work on my endurance so I can get more songs out.
I also need to work on breathing while I dance; three breaths for a 120s song is probably not a healthy rate. This is supposed to be aerobic exercise, not anaerobic.
In other news, I've finally got posting to LJ working decently. I write to my post-by-email address, copy the message body into a text editor, replace n (or rn, if I'm on a Windows box) with
, and paste that into ping.fm. Then I send the original message.
Conveniently, this gives me a place to put draft posts, even though I'm using ping.fm. Very nice.
(And while LJ strips my email signature, I leave it in for the ping.fm posts. I like it. That's why it's my signature.)
--
:wq
Saturday, March 13, 2010
Applying StumbleUpon to code.
Why would you want to random-walk a code base? I can think of a couple reasons. First, you're bored, stuck or stalled, and you need a distraction from the function you're working on. Second, perhaps you need to familiarize yourself with the code base a bit better better by randomly jumping around to different files, classes and functions.
Here are a few ways to identify a place in code, thinking strictly from a C++ perspective. (Other languages have their own ideal ways of thinking about code at a component level):
* File::Line
* Class
* Function
At a slightly broader perspective (from a Visual Studio perspective. Other development environments have their own terminology):
* Project
* Solution
Getting meta:
* Bug report
* Bug comment
Of course, a line in a file probably exists in association with a class, and with a function. So you would likely have an implicit relationship there. A class or function is likely to have a relationship with a project and solution (or several, if the file it exists in is shared among multiple projects). So there are more implicit relationships. A bug report may have some association with one of the other location identifiers. More implicit relationships.
So that's the content side of things. What about the user side of things?
StumbleUpon is Yet Another Social Network. You have contacts whose likes and dislikes affect where their recommendation algorithm sends you, and your likes and dislikes affect their browsing experience.
While the "social networking is going to solve all your business problems" fad went away with the dot-com bust, there's still some value in positional association. Let's say you've got a project development team of four people, and they all tend to work on the same product or product component. Or maybe you've got a company with thirty developers, and they're all working on the same gigantic codebase. That's akin to StumbleUpon's contacts.
While they're random-walking through their codebase, the developers' individual interests and disinterests would draw each others' attention to various parts of the code base, not as something to direct their focus on, but as something to let their brains passively absorb and toy with while they're taking a step back from the draining problem they're already focused on.
Anyway, just a thought.
--
:wq
Friday, March 12, 2010
Hardware RNGs
"cat /dev/urandom"
You'll get a flood of garbage data, then a trickle, then it will stop. You've drained the kernel's entropy pool. Move your mouse around (you're not doing this on some server, right?), and you'll see the trickle resume.
So you can get good random numbers by reverse-biasing a diode and listening for thermal noise, but you only get those numbers at a low rate.
That has to be the most trivially parallelizeable hardware problem I've read of in ages. How many millions of transistors can we fit in a 1mm
Thursday, March 11, 2010
So the new campaign world...
(Note, this isn't a final description, even of the parts I'm describing. Things are subject to change.)
Premise: The material plane is formed by the intersection of several other planes. The intersection is caused by a loop of (something) that acts somewhat like a gravitational field in a multidimensional space, drawing all the planes together, with the strongest point of intersection following the ring. (Not the interior of the ring, but the ring edge itself.) The ring itself is deep underground. (How deep? I dunno. Deep enough for dwarves to get at it, anyway.)
Whenever I talk about the ring, I'm talking about the actual torus itself, not the entire region it encompasses. Also, N, for now, is 20. I may scale it up or down. I don't know. "I" needs to be calculated based on the concept of the inverse cube law mentioned below, but I don't feel like doing the calcs right now.
There are six primary zones, relating to the ring:
* A2 -- Region 0-I miles from the ring.
* A1 -- Region I-2I miles from the ring.
* B -- Region 2I-(N-2I) miles from the ring.
* C1 -- Region (N-2I)-(N-I) miles from the ring.
* C2 -- Region N-(N-I) miles from the ring.
* D -- Region greater than N miles from the ring. There are two of these, one on the outer side of the ring, and one circular region on the inside of the ring, a sort of interior dead zone.
Notable artifacts of this:
* Magic is strengthened in proximity to the ring, though the strengthening effect fades according to an inverse-cubed law. (See "inverse square law", and bump it up a dimension)
Region D: magic has faded to uselessness, and the material plane has faded to void. Not space, not vacuum, just void. No rules of physics apply there. Some who've touched it are said to have ascended, while most are never heard from again.
Region C2: the material plane takes on a strong form of the chaos property. (It's been a while since I read the old 3.0 D&D splatbooks, but I remember there being a chaos plane or some such.) These are known as the "outer strangelands."
Region C1: the material plane takes on a weak form of the chaos property. These are known as the "inner strangelands."
Region A2: the material plane takes on the strong form of the "wild magic" property.
Region A1: the material plane takes on the weak form of the "wild magic" property.
Region B: the material plane behaves normally.
* Climate varies greatly near the ring
Region A1: Small, adjacent regions have very, very different climates. Storms are common as these incompatible climates mix at their boundaries.
Region A2: As with A1, but the climate regions are much larger.
Other notable things about the ring:
There are two tall mountains on the "south east" corner. One of them I've nicknamed "nattie" for the time being. Deep in the core of Nattie is an area where the hypermagic ring is twisted into a Gordian knot, leading to stronger localized effects. Closer to the ring's center is another mountain, which I've nicknamed "Everest." At an altitude fairly close to Nattie's peak, the "sun" (some bright light source; I haven't figured out exactly how hot it is) follows the hypermagic ring as something like a track. Day and night in the world are simply the sweeping of Everest's shadow as one, large sundial. The "dead zone" region at the center of the ring also casts a shadow; the lack of remotely consistent physics prevents light from traversing it. As a result, most of the world has two periods of darkness for every cycle of the sun.
There is one small anomaly at the "north west" corner. Dwarves dug deep under the surface of the world, and managed to intentionally create a loop twist of their own in one spot on the hypermagic ring. The hypermagic ring would very much prefer to remain circular, and so it will untwist itself eventually, given the chance. When that happens, all sorts of things will happen. That's not a key specified plot point, by the way; it's just a fact of the world. You make your own plots; I'm just defining the world at a static point.
There is one ocean covering the "south west" quadrant of the world, lined with a short region of hills followed by a mountain range. (The same mountain range that contains Nattie, Everest and the Dwarven magic project. The ocean extends from the outer C2 through the outer C1, B, A2, A1, inner A1, inner A2 and into the inner B regions.
The oceanic section of the A2 and A1 regions are considered perilous, and almost nobody crosses it except in times of emergency. Think of it like the dead region of wind flow near the equator as feared by wind-powered sailors hundreds of years ago, except that instead of a lack of motive energy, magic just goes wonky there.
Instead, trade between the south and west edges of the ocean follows two primary routes. One that sticks to the outer B region, and one that sticks to the inner B region. The Inner Sea is relatively crowded, with privateers and pirates, but also a large number of coastal trade points. The Outer Sea is fairly empty, but there's no room for error; if you have problems, or if you run low on supplies, you're either going to have to cross the A1/A2 regions to get to the Inner sea where you might find help, or you're going to be lucky enough to be near shore or "Atlantis" (nickname, natch) the island city that spans from the outer B region to the outer A2, used as a nigh-lawless research, trade and pirate stronghold.
At the border of outer B and outer A1, on the ocean shores, are the two largest port cities. The Inner Sea has ports that are far more numerous and dispersed.
...and that's all I have figured out for now.
Putting together a new campaign world
Wednesday, March 10, 2010
Tuesday, March 9, 2010
So I've put in nearly 3000 miles on my car in the last two weeks.
I think she (the car) likes it; she didn't give me a single complaint. I like driving distance. I'm looking forward to putting more miles on her at the right opportunities.
I have a family member who's pushing her car (A '91) to hit the 500k mark, and it's almost there. My 1996 Buick Regal has about 130k on it, but I'm not pushing for a mile marker, I'm pushing for 2016, when it will be 20 years old. Theoretically, it'd be eligible for a Michigan historical vehicle license. I bet I can still have her running as well as she is today. I get anywhere from 26 to 38 mpg, depending on road conditions and how I drive, but I haven't tracked my mileage too closely.
I like my car. We work well together.
Monday, March 8, 2010
Magnetized gorillapod
The tricky part is replacing a gorillapod foot with a magnet. My current though is to take the existing foot off the link chain, put the head of a bolt in the recess left behind, and secure the bolt by filling the recess with some sort of ceramic or plaster. Then I'd screw on one of these.
The only thing I really don't like about it is that, compared to my existing magmount, which uses one of these rubber feet, the magnetized gorillapod is going to be hell on surfaces I attach it to; K&J doesn't make the rubber feet for the right size of magnet, and I definitely don't need the 75lb of surface force provided by their 32mm mounting magnets, which is the smallest size they offer the rubber feet for. (I use one of those 32mm magnets as the basis to my existing magmount, and that's more than enough to keep my camera affixed to the top of my car while driving down the freeway. (By the way; the reactions you get from people when you start drivingdown the road with what looks like a DSLR on top of your camera can be hilarious; the magmount is low profile enough to not be obvious. I should paint the camera orange/black or something so people get the idea that it's supposed to be there.) So I've got two things to resolve before I build it. First, how to make plaster (or some better material equally as cheap to get/make/use.) Second, How to put a protective coating on the magnets so they don't scratch painted surfaces.
The problem I see with IPETEE
First, activity indicates activity. So you connect to a tracker that manages prohibited data. Prohibited how? Doesn't matter. Whether encrypted or not, you have a connection between you and a server managing prohibited data.
Ok, fine. You jump that hurdle by using something like Tor.
Second, there's more than just data, there's metadata. So you don't know what exactly is in a TCP or UDP stream, but you can learn things about it, just the same. What do you know about the packet size? Time between packets? Is a constant data rate maintained? How long does the connection last? Certain types of traffic aren't bandwidth-sensitive, but rather latency-sensitive. VOIP is going to have a distinct pattern. Torrenting is going to have a specific pattern. It's techniques like these that allow forensic specialists to detect hidden TrueCrypt volumes.
Third, encryption doesn't eliminate the data, it just obscures it, and not perfectly. Even aside from the possibility of cracking the encryption key, it's possible to guesstimate what kind of data an encrypted bitstream represents. I've read of that being used on encrypted hard drives, for example.
Thursday, March 4, 2010
Ground drove my computer loopy.
The flash upgrade had gotten me to the point where I could at least load boot sectors again, and I was able to run memtest off of live CDs, but I couldn't seem to boot into 32-bit or 64-bit Linux, either my installed version or from a couple Xubuntu live CDs.
I was beginning to suspect some sort of weird flash corruption that was preventing me from using graphics card features, or possibly from switching to protected mode or x64 mode. (I don't know how memtest86+ works, as far as accessing all 8GB of my RAM. I'm pretty sure the BIOS is still in Real mode when it runs its initial sweep, but maybe it's bouncing back and forth between Real and Protected during POST.)
The thought of another outlay to continue having a nice computer at home was not appealing.
Finally, a few minutes ago, I realized something. I had two relatively new pieces of hardware attached to the computer: An APC UPS and a powered USB hub. I disconnected the USB connection between the UPS and the computer, and disconnected the hub, and rebooted the computer. The 32-bit Xubuntu live CD came right up. Huh. Reboot, throw in the 64-bit Xubuntu live CD, and *that* came right up. Huh.
I haven't tried booting off my hard disk yet, and I think that'll require some grub command-line magic to deal with device reordering stemming from the BIOS upgrade and CMOS changes. However, I think it's ultimately workable.
What I think happened is that the connection of the UPS and the powered hub to the computer via USB led to a ground loop that was messing with the internals of the USB controller on the motherboard. See, the powered hub isn't plugged into the UPS; it's a fair bit away from the computer, and I'll have to run an extension cord to get the UPS's power to it. As long as the operating system didn't try to do too much with that USB controller, things worked fine. That meant I could get into BIOS and tweak things, and it meant I could get into grub and memtest without too much trouble. Well, sortof. Remember how, before the flash upgrade, the system would hang at a random point between POST and loading the bootloader. I think the flash upgrade may have changed part of how it dealt with the USB controller, with the newer version inadvertently working around some of the ground-loop-induced weirdness.
So, yeah. A little more experience for those weird situations.
Depth perception and optics
On the other hand, there's this idea I had...
*sidetrack*
It stemmed from thinking about image stacking in HDR photos. Image stacking is simply taking several photos of the same object, where the only change between them is a known, measured characteristic of the photograph recording. Typically, in HDR, it's your exposure adjustment, or how much light you demand your camera collect before saving off the frame. Since your camera's sensor can only precisely measure a finite range of light levels, taking several frames where you move that range around allows you to increase the amount of detail you've captured in bright and dark areas.
However, image stacking needn't *only* be done with exposure adjustments. The concept of stacking applies for any variable you can measurably control while observing a scene, and it just happens that exposure adjustment is the most immediately useful setting to vary.
*end sidetrack*
*second sidetrack*
And now a brief bit about aperture width and depth-of-field. A camera's aperture is the hole that allows light to pass through and land on its sensor. It's exactly analogous to your pupil. The larger your pupil, the more light passes through and lands on your retina. The smaller your pupil, the less light lands on your retina.
One weird side effect of optics and aperture size, though, has to do with focusing. With a narrow aperture (such as when you're outside on a bright, snow-covered day), your depth-of-field is very large, meaning that you can see near objects in focus just as well as you can see distant objects, with no additional effort on the part of your lens. (either that of your eye or of your camera) On the other hand, when the aperture is very wide (Indoors, lights off, etc.), the depth of field is very narrow. That means that you (or your camera) need to adjust the configuration of your lens in order to focus on near or distant objects, regardless of whether you have one or two eyes.
All this boils down to one interesting fact: You can know where your field of focus is if you know your aperture size and your lens configuration.
*end second sidetrack*
What all this means is that you could take several images, each with known aperture and lens characteristics, and learn how far away objects in the scene are simply by observing how in-focus each area of your scene for each known field of focus.
So, yes, you could have calculable measured distances to objects in your scene simply by stacking images of that scene where you know the focus range of each of those snaps.
Honestly, though, I think this applies more to machine vision than human vision. It's also probably most useful right now for telescopes.
A quick note and idea on fuel efficiency...
When I was driving to South Carolina and back, I discovered I was going 80mph without pushing the car's engine much at all. (The amount of work I was asking the engine to do might have kept me going 55 or 60mph, normally. Maybe 65mph on the average downgrade on I-77.) It took me a while, but I finally came up with a plausible reason this happened.
I had merged onto the freeway, found myself embedded in a large pack of big-rigs semis, hadn't settled into traffic enough to set cruise, and had to move to get out of the way of traffic shifts to let another batch of traffic merge in. I signaled, changed lanes to the left and accelerated--and felt my jaw drop when I saw I was effortlessly going 80mph.
What I think happened was that the sparse pack of semis (and filler of smaller vehicles) spanning three lanes had caused the volume of air covering I-77 to be moving roughly uniform in line with traffic, not too far from the speed of traffic. In effect, the traffic had created its own wind tunnel, and you didn't have to be dangerously close to the back-end of a semi to get a drafting effect.
So what would happen if you took a long stretch of road (such as an under-river or through-mountain tunnel) and set up blowers pushing air in in the direction of traffic flow? Given the reduction in air drag, how much would you save on fuel economy? Would the energy involved in maintaining a 15mph tail wind in dense-traffic areas be greater than the aggregate saved energy in vehicle fuel? How much of an impact on local pollution would it have? By pulling energy from the electrical grid rather than car engines, you can move the atmospheric cost of energy generation away from areas where it could cause health problems. (Places with high pollution due to vehicle emissions might find that useful...)
Anyway, it was an interesting experience, and leads to a lot of interesting questions.
Wednesday, March 3, 2010
I finally realized why shutter glasses make sense.
So do polarized light systems like IMAX's linearly-polarized glasses, and Real3D's circularly-polarized glasses.
So why do shutter glasses make sense? There's nothing about the concept that limits you to two video channels. You could have four, or eight, or even sixteen, once the technology's chronometric precision increases enough. It's time-division multiplexing for the visual field.
That's going to have major, major implications for video games. No more splitscreen forcing you to have only half or a quarter of your normal visual field; you and your three buddies can each have the full frame to themselves.
It might even give rise to a new form of cinema, one where both the protagonist's and antagonist's stories are told at the same time, but the viewer has to choose which one they're watching.
Monday, March 1, 2010
Software vs hardware RAID
The RAID support that comes built-in with your motherboard is *probably* software RAID implemented in your system BIOS. Most small RAID cards have their functionality implemented in on-card BIOS that gets loaded when the system boots. As with system-software RAID setups like md, these RAID setups consume your system CPU and RAM as they churn to perform the calculations associated with your RAID configuration, including things like ECC and parity calculations.
All of this is best-known as "software" RAID.
The funky thing? "Hardware" RAID is also done in software, albeit software that executes on a dedicated processor on your RAID card. (As opposed to your system CPU.) You upgrade this software whenever you upgrade the firmware on the card.
So here's what I'd like to see...An Open Source hardware RAID card. All it would amount to is a multi-port SATA controller connected to an onboard CPU, passing data back to the host operating system via the PCIe bus.
The firmware would be built by, well, I dunno. The folks who like md, but don't like running it on their core system. The folks who want to play around with experimental RAID configurations and ideas. The folks who want to try putting LVM into "hardware." There are plenty of possibilities.
Put a fallback firmware set on the card, in case of flash upgrade failure, to avoid bricking the thing.
I'd hit that.
Saturday, February 27, 2010
Loving "Baccano!"
- The characters are colorful -- "Yeah, that was impossible. At least we did the next best thing, stealing the entrance!" "Guns? Guns? I hear guns! This is getting exciting! This is getting exciting!"
- The dialog is a blast -- "YesYesYesYesYesNoNoNo, Still no, Hell No!"
- The animation is excellent -- See Ladd Russo's initial fight in the dining car.
- The story presentation is a blast -- Three stories presented concurrently, containing some common characters. Many scenes get revisited from different characters' perspectives. Most of the story is presented out of chronological order; if it weren't different parts of the stories would spoil parts of other stories.
- Set in the late 1920s/early 1930s.
- There's a lot of violence. You may or may not enjoy it.
Friday, February 26, 2010
A realization...
Wednesday, February 24, 2010
HDR of a Charleston alleyway
Thursday, February 18, 2010
Mix tapes for driving.
Yes, tapes. My laptop's being repaired, and I don't have any other decent audio player device at the moment.
To make these tapes, I created a playlist of songs in Rhythmbox that I would be willing to listen to. I don't know how many are there, or how many minutes' worth of music is there. Suffice it to say it's a lot. I also threw in all of the ads and callsign announcements from Streets of SimCity, because they give me a chuckle. I have the playlist playing in Shuffle mode, and I have a dual-tape deck sitting between my computer and stereo syste, configured to continuously record, looping through all four sides of tape.
When I wake up, I'll pop the tapes out. They'll have six hours worth of music on them, and I won't really know what's on there and when.
This will be interesting...
Wednesday, February 17, 2010
Picked up a Wiimote today.
The mapping I have in mind:
- As long as the trigger is being held, its motion will affect the mouse cursor's position. When the trigger isn't being held, the mouse cursor's position isn't affected.
- The D-pad will be up/down and left/right scroll events.
- The A button will be the Left mouse button. That leaves buttons 1 and 2 for Right and Middle.
Monday, February 15, 2010
A notice to the DIY folks.
Don’t let this happen to you.
Women often receive warnings about protecting themselves at the mall and in dark parking lots, etc. This is the first warning I have seen for men. I wanted to pass it on in case you haven’t heard about it. This will only become more commonplace.
A ‘heads up’ for those men who may be regular Lowe’s, Home Depot, or Costco customers. This one caught me by surprise. Over the last month I became a victim of a clever scam while out shopping. Simply going out to get supplies has turned out to be quite traumatic. Please, don’t be naive enough to think it couldn’t happen to you or your friends.
How the scam works:
Two seriously good-looking 20-something girls come over to your car as you are packing your shopping bags into the trunk. They both start wiping your windshield with a rag and Windex, with their breasts almost falling out of their skimpy T-shirts. It is impossible not to look. When you thank them and offer them a tip, they say ‘No’ and instead ask you for a ride to McDonald’s. You agree and they get into the back seat. On the way, they start undressing. Then one of them climbs over into the front seat and starts crawling all over you, while the other one steals your wallet.
I had my wallet stolen November 4th, 9th, 10th, twice on the 15th, 17th, 20th, 24th, & 29th. Also December 1st & 4th, twice on the 8th, 16th, 23rd, 26th & 28th, three times last Monday and very likely
again this upcoming weekend. So tell your friends to be careful. What a horrible way to take advantage of men.
Warn your friends to be vigilant.
P.S. Wal-Mart has wallets on sale for $2.99 each. I found cheaper ones for $1.99 at K Mart. Also, you’ll never get to eat at McDonald’s. I’ve already lost 11 pounds just running back and forth to Lowe’s, Home Depot, and Costco.
Adaptive keyboard layout
Now, I'm a QWERTY touch typist. I can get by just fine on a blank Das Keyboard, if you give me a QWERTY layout. I realize, of course, that a lot of folks prefer DVORAK; having your more-frequently-used keys on home-row has to be great.
Even as a QWERTY touch-typist, I think there may be room for improvement. Consider the advantage Dvorak offers, with the most-frequently-used keys on home row. That only works under an assumed use case, which may or may not be accurate depending on anything from your locale to how you normally use a computer.
Let's say your keyboard kept a running record of your last twenty-thousand keystrokes. Every time you pressed a non-modifier key, it would push that key on to the queue, pop the twenty-thousand-and-first key off, and then run the entire buffer through huffman encoding.
The keyboard now has an internal representation of which characters you use most frequently, in the form of a huffman tree. Because it knows its own physical form factor, it can estimate the cost of each key on the board based on how much travel there is from home row to that key.
Simply sort the key cost in ascending order, and then walk through the huffman tree, assigning each character encountered to the least-cost key remaining.
You now have a possible keyboard layout optimized specifically for you and your use case.
For me, what I'd like the keyboard to do (at that point) would be to sit tight unless it discerns that a cost reduction threshold would be crossed; say, 10% cost reduction compared to my current activity and use case. At that point, it should beep at me, or flash a little light. Once I acknowledge, the keyboard layout would change.
Of course, something like this would depend on a visual feedback mechanism; I would have to be able to quickly see what the keys were remapped to. Under normal circumstances, the rearrangements shouldn't be much, and most of the layout would remain the same. I should only need to note that two or three keys (not key pairs, mind you) changed places.
I'd want to switch away from typing my password in, though; someone could get a lot closer to guessing it by noticing one or two strange characters that are closer to my home row than for most.
There's also the round-robin key buffer, which I think may be necessary for preventing old keystrokes from polluting the huffman tree. Perhaps simply randomizing which key in the buffer is replaced would be sufficiently optimal for the purpose, rather than storing keystrokes in order.
I think I could get used to a keyboard like that.
Sunday, February 14, 2010
LOLCODE and GAFFERS
We never did see any submissions of LOLcode, but that's beside the point; it's technically possible, because a working implementations do exist.
The reason I'm remembering this today is the discussion of a language named GAFFERS that's recently shown up on the site. There was question of whether or not the language was a hoax, as one of the editors didn't turn up any reliable references while looking it up. I dug into the information provided and didn't find anything to back it up. It appears to have simply been a prank by a vandal. (Not a particularly good one, either; if they'd at least have gone to the trouble of creating convincing-looking references, I might have been amused and impressed.)
If the LOLCODE want to try their hand at getting a decent task coverage on Rosetta Code, they're welcome to. Just follow the steps for adding a language.
If whoever is behind GAFFERS wants to, well, they've got to show an implementation first.
Things I hate about posting to Facebook.
Except Facebook. And that's not entirely ping.fm's fault.
With Facebook, I can't post a "note" (Called a blog entry anywhere else) that has text content, followed by an embedded video, followed by text content. At best, ping.fm can convert that to a video post with attached text. At worst, it'll show up as the raw HTML data for embedding the video. I've found I prefer the latter approach, because there's *no* other way to embed multiple videos.
Also, Facebook's HTML subset is ridiculously limited, almost as bad as Slashdot JE's. (At least FB allows inline images!) That means that simple formatting instructions that might otherwise have worked fine, like the "div" blocks that were (and maybe still are? I stopped using them) used by places like blogthings get defanged and look as ugly as embedded flash videos. No, I don't want to add an app to show that particular survey. No, I don't want to add an app for the "which character/what personality type/what are your politics" widgets. Facebook app privacy is so ridiculously poor, I can't even refuse to add the stupid things in defense of my own privacy; Farmville and Mafia Wars already have access to my profile information, just because my contacts added them.
You think Google is a privacy threat? At least a savvy person can use them while not giving them data, thanks to their preference towards open protocols and open APIs. With Facebook, use it or lose it. I got a Facebook account to deal with all the invites I was getting. It's also the de-facto way of staying in passive touch with people you've known from the past; the modern replacement of the Rolodex.
I love being a geek...
(10:26:14 AM) Mike: I found part of the source of our communication problem!
(10:26:30 AM) Mike: http://tvtropes.org/pmwiki/pmwiki.php/Main/BuffySpeak
(10:36:41 AM) J: :)
(10:37:12 AM) Mike: "BuffySpeak" should be our clarity codeword from now on. It'll drive T nuts. :D
(10:37:29 AM) J: lol
(10:37:35 AM) J: thas almost enough reason to do it :)
(10:37:42 AM) J: probably drive me more nuts though
(10:38:30 AM) Mike: Hey, it's faster than "You're using too many unresolved pronouns!" or "Linker error: symbol 'thing' is ambiguous."
(10:38:53 AM) J: Hey, I like the 2nd
(10:39:03 AM) J: I imagine that P would fall in love with it
(10:39:17 AM) Mike: *chortle*
(10:39:24 AM) Mike: I love being a geek.
(10:39:44 AM) J: chortle?
(10:39:47 AM) J: seriously?
(10:39:52 AM) J: I havent heard that in years
(10:39:59 AM) ***Mike double-checks the definition.
(10:40:07 AM) Mike: er.
(10:40:11 AM) ***Mike inverted that one.
(10:40:20 AM) Mike: What's 1/chortle?
(10:40:33 AM) Mike: You know, reversing the amplitude, but not the sign?
(10:40:34 AM) J: Umm, you used it correctly. its just obscure afaik
(10:40:43 AM) J: um, no idea
(10:41:15 AM) Mike: ROFLMAO, I suppose, except it wasn't quite that strong.
Saturday, February 13, 2010
Loving "Baccanno!"
"That was our first kiss!"
"Wait, you two have been an item for ten years, and he never kissed you? I mean there's gentlemanly, and then there's stupid! Hey! I'm talking about you, too, 'princess!'"
Friday, February 12, 2010
Why having been a tutor does not mean you communicate well.
It didn't, and doesn't.
As a tutor, my chief strategy was to provide the student with all the bits and pieces of information required to build an understanding of what they were trying to do, but to systematically avoid actually connecting the dots for them. I found that that system worked very well for the students who wanted an understanding, not just a grade. (Which of those two types of students were normally the ones to come in for tutoring is a topic best avoided.)
It's only taken me three years of real-world experience to realize that while that coworkers aren't students, and I need to explain my thought process, rather than teach it.
In fact, that's probably a good habit to get into outside of work, too.
So I finally sent my laptop in for repairs.
Before sending it in, I put on a blank install of xubuntu, a weak password, auto-login, and had Firefox automatically start, maximized, with a local homepage including a complete description of the problems, and localized playback (which I tested without network access) of the above photos and video. I also explained some things they could skip, being merely cosmetic fixes, and told them not to bother putting Windows back on if it was going to be a hassle for them. (I didn't have a restore CD to provide.)
Since all the problems I've been seeing are based in hardware, they should be able to either fix it or declare it a lost cause. If they declare it a lost cause, my warranty says I'm supposed to get a replacement or check to go towards a replacement, so it's no skin off my teeth.
It'll be interesting to see what happens.
Thursday, February 11, 2010
Awsome. Just awesome!
Well, not exactly this. They're using Pentium-class cores, where our discussion compared i686 and i386 cores.
I'm torn on their using a 32-bit core as a base, though. I spend enough time on 4GB+ PCs that I loathe the idea of dropping back to a 32-bit memory model, though; There really is an advantage to having more than 4GB of directly-addressable address space.
Wednesday, February 10, 2010
Benefits of tech support
While doing phone tech support can be a grating, humiliating, degrading experience, if you do it right, it can also be incredibly rewarding; I just came across a couple Thank You notes that were sent to that ISP years ago, addressed to me. A couple years ago, one of the people I helped as part of my current job sent the company a fruit basket.
Whatever you do in life, if you're helping someone as a matter of course, chances are it's a worthwhile habit. If you're lucky, they'll remind you of that fact.
Monday, February 8, 2010
Watched Avatar again yesterday...
At the point, a researcher is trying to teach Jake Sully the intricacies of the Na'vi language. It goes something like this:
Researcher: (Na'vi)
Jake Sully: (Na'vi) (incorrectly pronounced)
Researcher: (repeats)
Jake Sully: (repeats), looks up with an exasperated grin.
Researcher: "Literally, it means 'I see you,' but it's not just 'I see you before me', but 'I see into you.'"
While a well-spent ten-seconds of film, I think that would have been a heck of lot funnier/more interesting/whatever as:
Researcher: (Na'vi)
Jake Sully: (Na'vi) (incorrectly pronounced)
Researcher: (repeats)
Jake Sully: (repeats), looks up with an exasperated grin.
Researcher: "Literally, it means 'I see you,' but it's not just 'I see you before me', but 'I see into you.' Like 'grok.'"
Jake Sully: "'Grok?'"
(And would have had a nice side-effect of catapulting 'grok' back into popular awareness...)
Saturday, February 6, 2010
"real men just upload their important stuff on ftp, and let the rest of the world mirror it ;) "
I've been thinking about a recurring issue...Namely that none of RCo's remote backup targets are very good. My home system has a problem remaining alive for any extended duration, and I don't have any other good prospective places to I can trust to send the data. (No offense to anyone who's offered, but it's hard for me to totally trust someone I've never met in person.*)
I may have hit on a novel solution, but I want to run it past a bunch of people (namely, you), before I do something this crazy.
Step 1: Take backup on server
Step 2: Compress backup to tarball.
Step 3: Encrypt tarball using a GPG and a long, long public key.
Step 4: Build a torrent.
Step 5: Add torrent to RSS feed.
Step 6: Anyone who wants to help can point their torrent client at the RSS feed. Data's encrypted, so I don't have to worry. With enough seeder boxes out there, there can be several full copies out there.
Bonus: Server data migration happens much, much faster. :)
* Yes, this is me we're talking about, and I realize the irony.
Friday, February 5, 2010
Cool trick of the day: "Uploading" URLs.
So you want to upload a file to some web form. Click Browse, that traditional file upload dialog pops up.
Into the "Filename" field, type (or paste) the full URL to the file you want to upload. For example, if the file already exists on Flickr or some other site, and you have the URL to the file at that location, paste it here.
Click Open; the dialog will appear to hang for a bit, but that's because it's downloading the file to your local system. When the dialog disappears, the path to its local location will appear in the upload field.
Proceed with however you would normally use the web form; the file was already copied to your local system, Firefox knows where it is, and it will be uploaded when you submit the form.
Wednesday, February 3, 2010
So the EFF is doing a fundraiser, hosted by Adam Savage.
Man, I wish I could be in SF next week.
EFF, Adam Savage, but best of all? JWZ. His screensavers package was the reason I dropped gaming on my Win95 box over a decade ago and switched to Linux.
Linux answers the greatest of questions.
shortcircuit@dodo~
01:35:48 $ whoami
shortcircuit
shortcircuit@dodo~
01:35:50 $ who
shortcircuit tty7 2010-01-30 18:29 (:0)
shortcircuit pts/0 2010-02-02 20:32 (:0.1)
shortcircuit pts/1 2010-02-03 01:28 (:0.1)
shortcircuit pts/3 2010-02-03 01:30 (:0.1)
shortcircuit@dodo~
01:35:52 $ whois shortcircuit
No whois server is known for this kind of object.
shortcircuit@dodo~
01:35:55 $ whatis shortcircuit
shortcircuit: nothing appropriate.
shortcircuit@dodo~
01:35:57 $
Tuesday, February 2, 2010
That's going to smart.
Dear Google Apps admin,
In order to continue to improve our products and deliver more sophisticated features and performance, we are harnessing some of the latest improvements in web browser technology. This includes faster JavaScript processing and new standards like HTML5. As a result, over the course of 2010, we will be phasing out support for Microsoft Internet Explorer 6.0 as well as other older browsers that are not supported by their own manufacturers.
We plan to begin phasing out support of these older browsers on the Google Docs suite and the Google Sites editor on March 1, 2010. After that point, certain functionality within these applications may have higher latency and may not work correctly in these older browsers. Later in 2010, we will start to phase out support for these browsers for Google Mail and Google Calendar.
Google Apps will continue to support Internet Explorer 7.0 and above, Firefox 3.0 and above, Google Chrome 4.0 and above, and Safari 3.0 and above.
Starting this week, users on these older browsers will see a message in Google Docs and the Google Sites editor explaining this change and asking them to upgrade their browser. We will also alert you again closer to March 1 to remind you of this change.
In 2009, the Google Apps team delivered more than 100 improvements to enhance your product experience. We are aiming to beat that in 2010 and continue to deliver the best and most innovative collaboration products for businesses.
Thank you for your continued support!
Sincerely,
The Google Apps team
Email preferences: You have received this mandatory email service announcement to update you about important changes to your Google Apps product or account.
Google Inc.
1600 Amphitheatre Parkway
Mountain View, CA 94043
Monday, February 1, 2010
WaitForSingleObject
Me: "WaitForSingleObject?"
Coworker: "Yeah."
Me, to boss: "He's got a handle on you."
Boss: *facepalm*
Coworker: *grabs a large piece of equipment*
Me: *ducks*
Sunday, January 31, 2010
Ok, what was the name of that thing?
Consider an NxN square, where no cells are blocked, and every row and column contains a whole word.
There's a specific name for those; they're notable because there are few known solutions for each N. I can't remember the name!
Thursday, January 28, 2010
Wait, what?
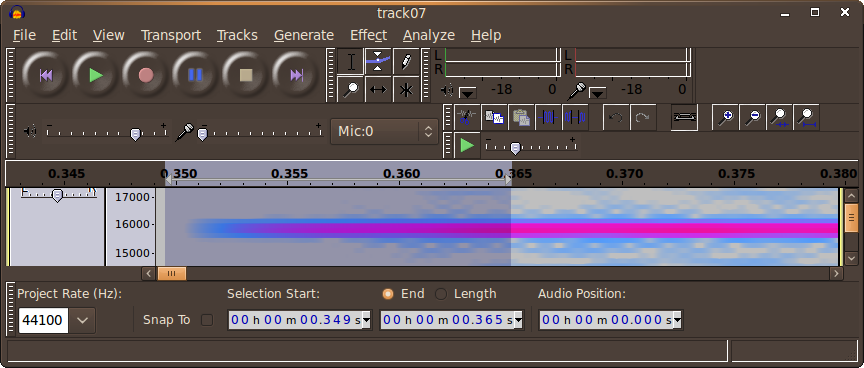
This is a zoomed in view of a particular part of the spectrum, as shown in Audacity. It's a solid, loud 16kHz present through nearly all of the song. At the volume I was listening at, it was painful!
I doubt it's an encoding artifact; The CD was ripped to FLAC. Here, I imported the FLAC into Audacity.
I don't know if the master was like this, or if I wound up buying a counterfeit disc.
Wednesday, January 27, 2010
Colonel Panic!
A couple workarounds are available to deal with this; You can set up a serial console so that system messages get dumped via good old RS-232 to another machine, or even a console on your parallel port so that the messages get printed.
Don't try that last unless you don't mind going through a ton of paper, and have ways of dealing with the printer noise.
It occurred to me, a few days ago, that x86 systems have a (very) small amount of non-volatile RAM, battery backed by the same battery that keeps your computer from losing time when you power cycle it.
While that amount of memory is very, very small, it may be large enough to hold a Panic message; That'd be a nice place for me to be able to look to investigate why my computer randomly hard-locked one evening while I was away.
Tuesday, January 26, 2010
Some mnemonics for "ls" parameters
ls -ltr # Sort by time, reversed, show more details.
ls -Ssh # Show and sort by human-readable size.
ls -Ssl # show and sort by human readable size, but show more details.
Graphic background doubles nicely as a desktop background
Monday, January 25, 2010
Fast track to a massive parallel computer
I've been thinking about parallel computation for for a while, and looking at different ways to do it. The best explicitly-known parallel computation setup out there are the @home projects like SETI@Home and folding@Home. These projects divide their workload into chunks, pass those chunks around, and programs running on volunteers' computers take these chunks, chew on them and pass them back.
A few weeks ago, I had the idea that someone could distribute an @home-style client as a flash applet using the one distribution mechanism many of us already hate--website banner ads. Have a flash applet distributed via advertising networks that:
- Connects to a central server
- Grabs a data chunk
- Chews on it
- Uploads the results to the central server
Flash already allows applets to pull remote files and perform GET requests. (I don't know about POST, though.) All that remains is grabbing and running the workload, and have a server that can verify that the workload results are uncorrupted. (i.e. not tampered with.)
Yes, this results in spinning an end-user's processors more than they would be otherwise, which may cost them a few more cents per month on their electric bill, or a notable reduction in their laptop's battery life. It would be helpful if Flash had a mechanism to change applet resource consumption based on system power state and/or user preferences. Still, yes, it's coopting a user's computer to do something they didn't explicitly agree to. Someone else can deal with the ethics; I'm just spouting an idea.
Also, yes, a large number of pages are only loaded for a very short period of time; The amount of time required to process a chunk of work may well require more time than the page will be loaded (and, thus, more time than the applet will be running). There's a workaround for that, too. First, Flash allows applets from any given domain to store a configurable amount of non-volatile data on the user's machine; That could be used as a data store for intermediate state. Second, the applet could wait a couple minutes before beginning the number crunch, looking for times when a page is left loaded for an extended duration. (Quite likely on sites like Youtube, Pandora and others with streaming media.)
![[HSV Rmx] Cosplay - AWA14 - L and Misa Amane](http://farm5.static.flickr.com/4068/4549660008_a8749e4e01.jpg)
![[HSV Rmx] Cosplay - AWA15 - Lara Croft](http://farm5.static.flickr.com/4059/4549660006_7d36115bfa.jpg)
![[HSV Rmx] Me](http://farm5.static.flickr.com/4064/4549660002_0f2de40af0.jpg)
![[HSV Rmx] Hair grows](http://farm5.static.flickr.com/4044/4549659978_68c5c0df1a.jpg)










